About 4Passwords
4Passwords.com is founded in 2017 by MCCS and MCCS is a Thycotic Certified Partner sinds 2010. After many Secret Server implementations over the years, we recognised that next to providing professional services for on-premise deployments, that there is also need for hosting and a hosted edition of Secret Server.
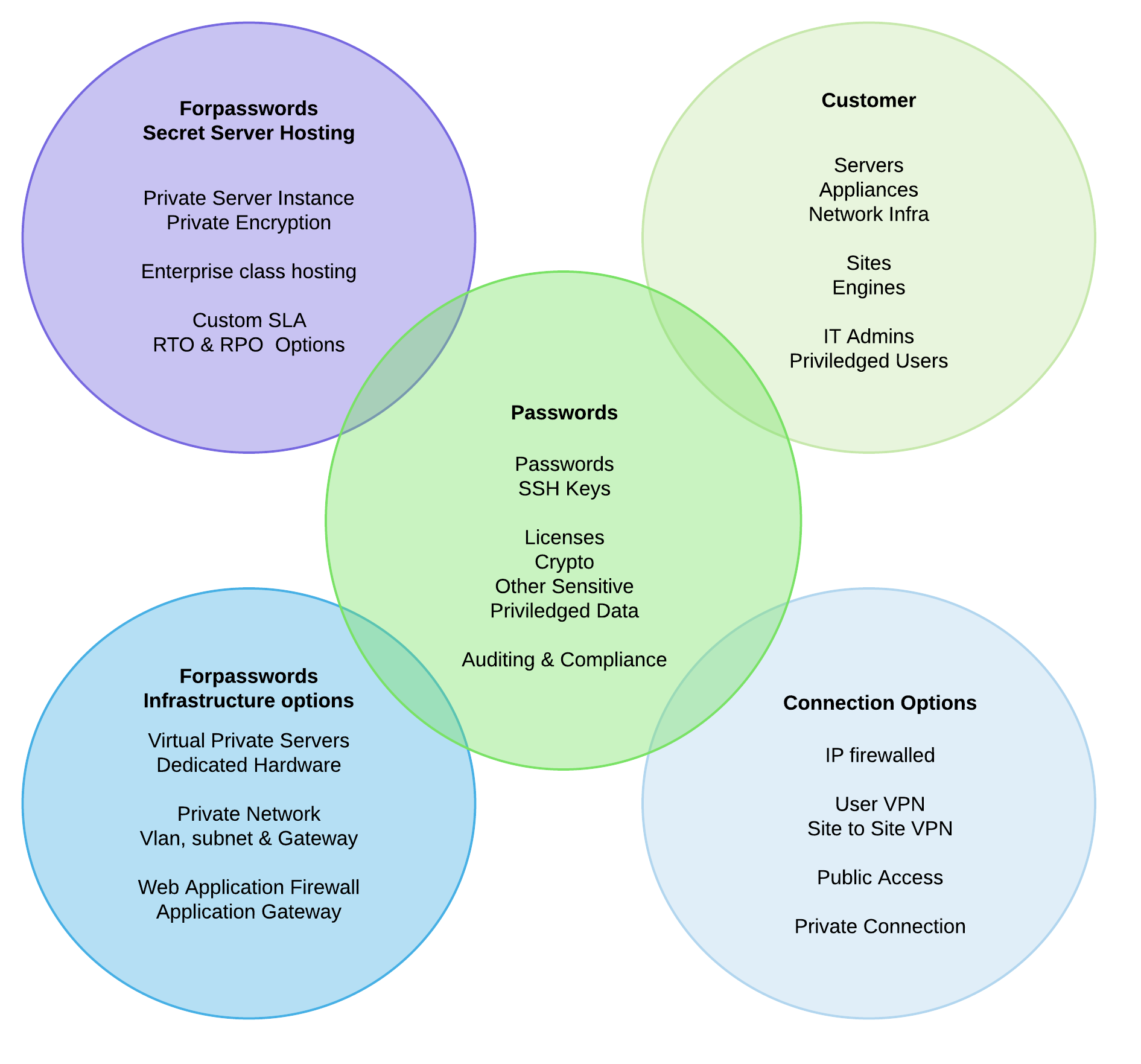
We developed an AVG/GDPR compliant work method with a redundant datacenter design to host private editions of Secret Server.
Every client gets their own private web instance, encrypted database and a separately stored encryption key
Flexible, A worry free service
No need to install, configure or invest in infrastructure and/or software licenses.
Affordable
Excellent services at honest prices.
Top-level Security
Exceed auditors expectations.
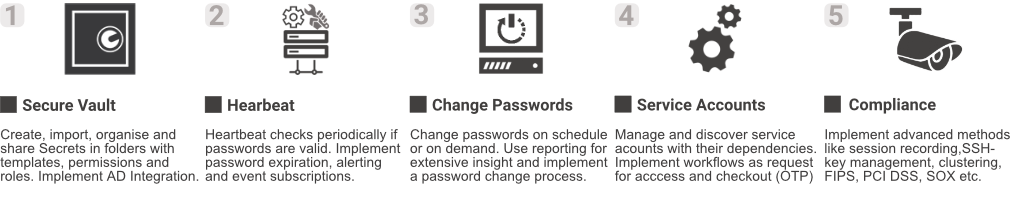
The implementation plan
Fast, easy and scalable deployment. Implement and finetune as needed.
Over the years we have completed many Secret Server installations and The installation is quick, you are literally up and running within the day.
To complete the implementation, we follow these 5 major milestones. in a secret server implementation
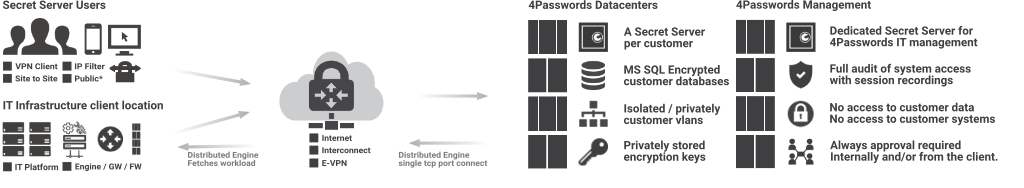
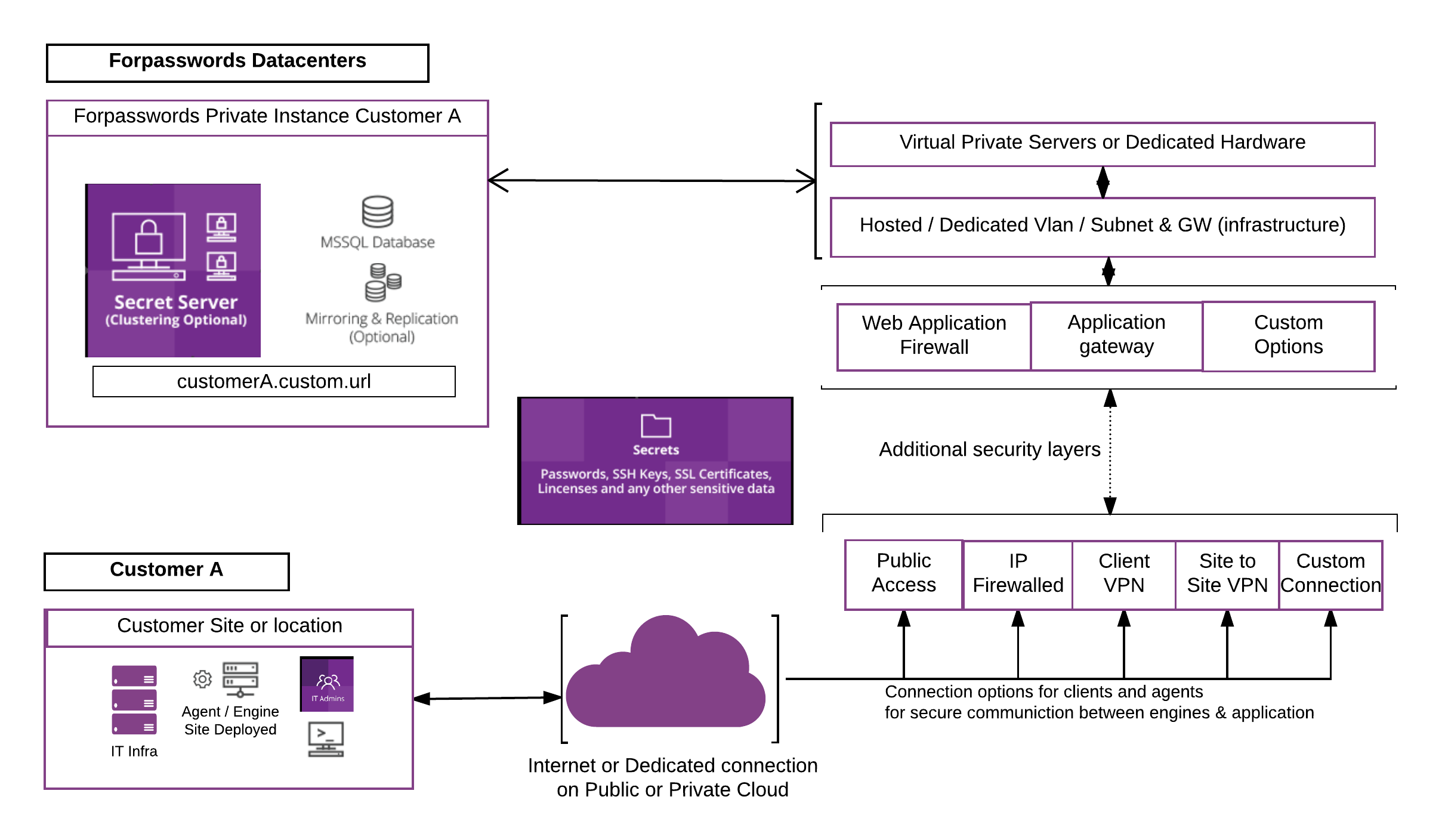
4Passwords hosting architecture
We host our infrastructure in private EU & US tier 4 datacenters with the highest level of physical security.
Optionally if desired we provide hosting in public clouds like Amazon, Azure & Google.
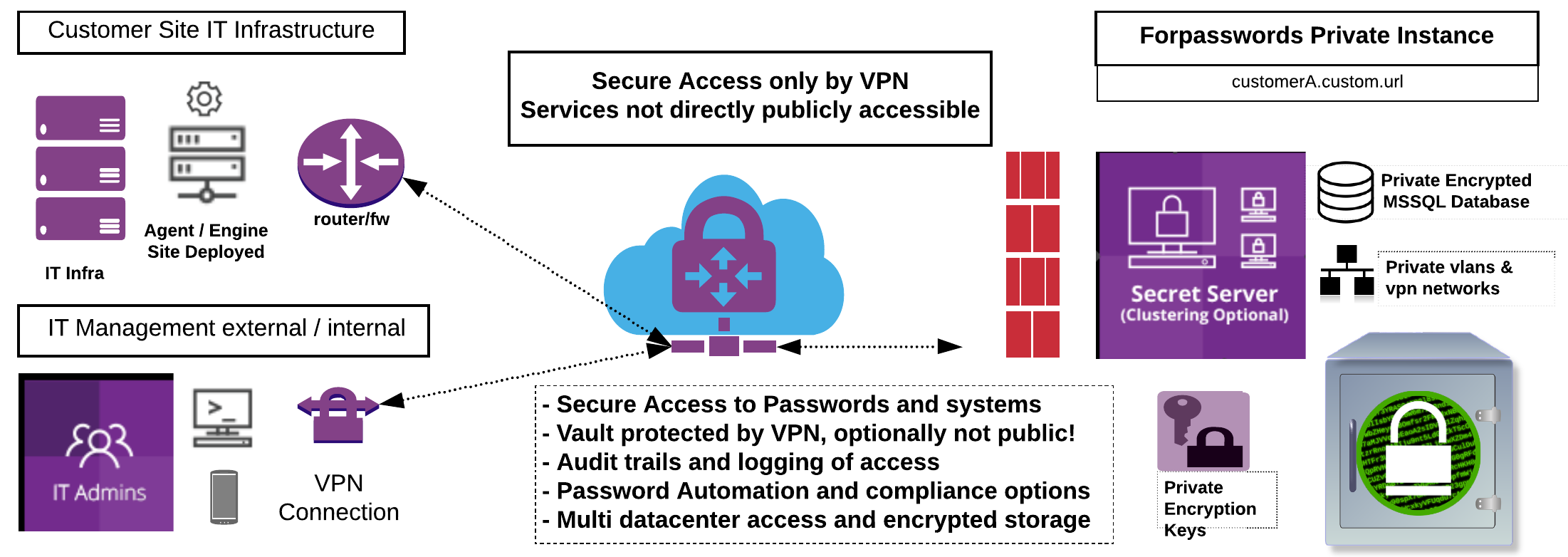
The hosted edition of Secret Server can be accessed securely with a SSLVPN client, site to site VPN connection (IPSEC) or a direct linkup with our data centers (Interconnect or E-VPN).
Security automation to IT Infrastructure can be realized with the Distributed Engine that communicates across the internet with a single TCP port and authenticates with a private / public key and IP whitelist. A site to site VPN can be added as an extra security layer to extra encrypt communications from and to the clients IT infrastructure and the 4P data centers.
For the Secret Server user, SSH & RDP Proxy tunneling techniques can be used together with the Distributed engine and VPN to allow access to secret server and IT systems securely from the web browser with full auditing & recording
As we host a private Secret Servers, we have setup our IT management in such a way so that our IT engineers never have access to customer data and/or access to client systems. All access to 4Passwords systems are managed by a dedicated Secret Server with full auditing and session recording. Approval for access is always required internally and/or from the client. We work with a 4 eyes principle, so no single person can access the 4Passwords systems, storage, backups or the privately stored customer encryption keys at any time independently.